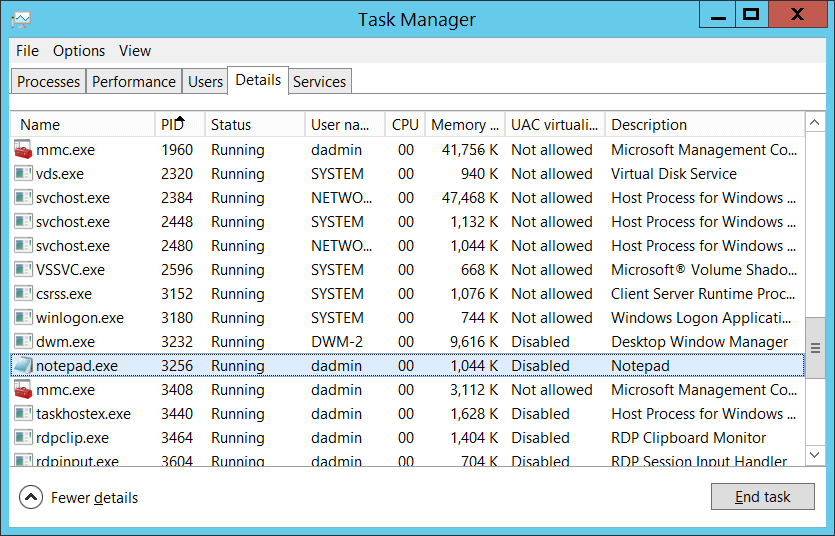
windows - EVENTID 4648. Mismatch ,Subject (Standard User), CredentialsUsed (Admin), Target(Localhost) - Server Fault
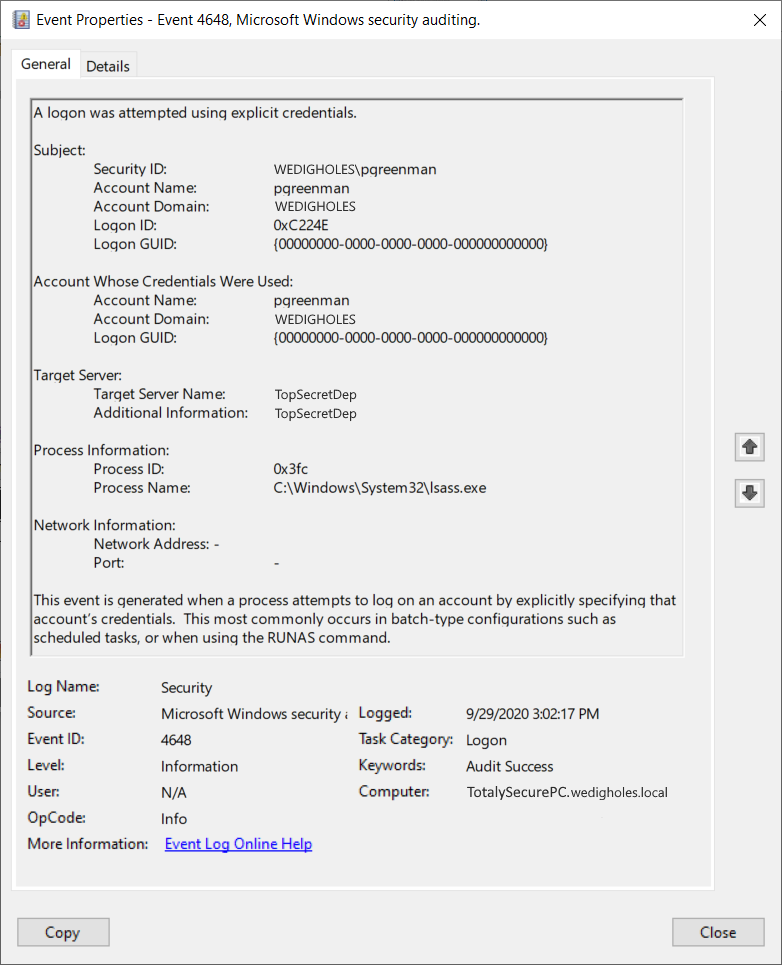
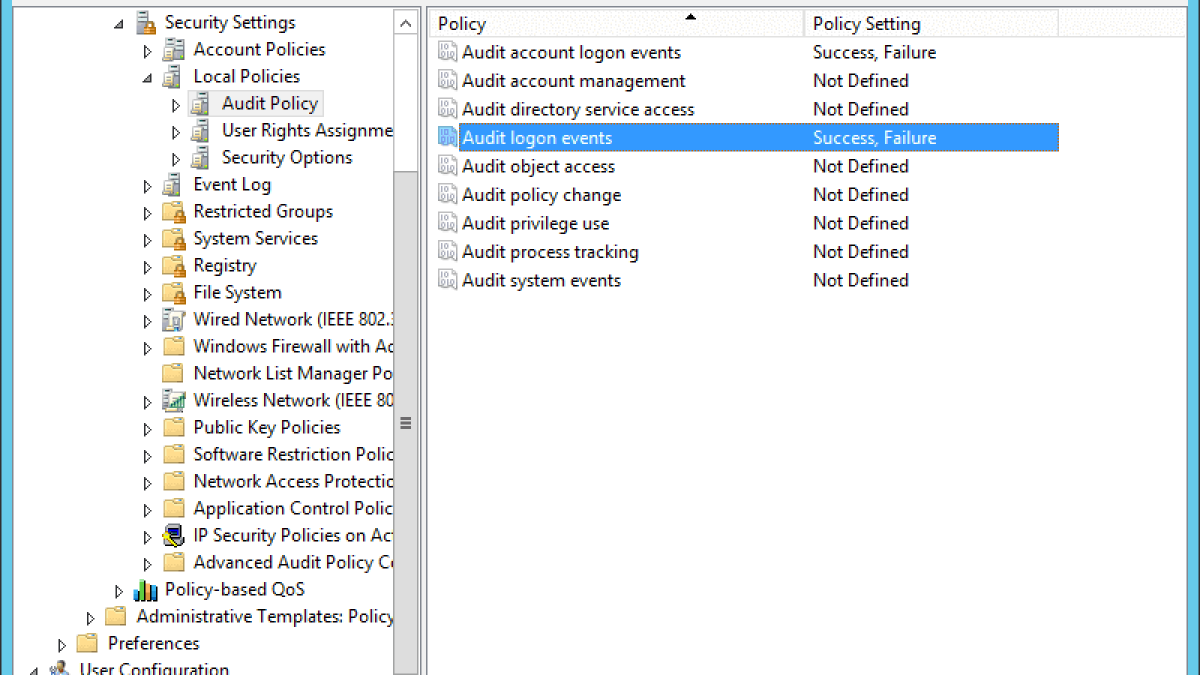
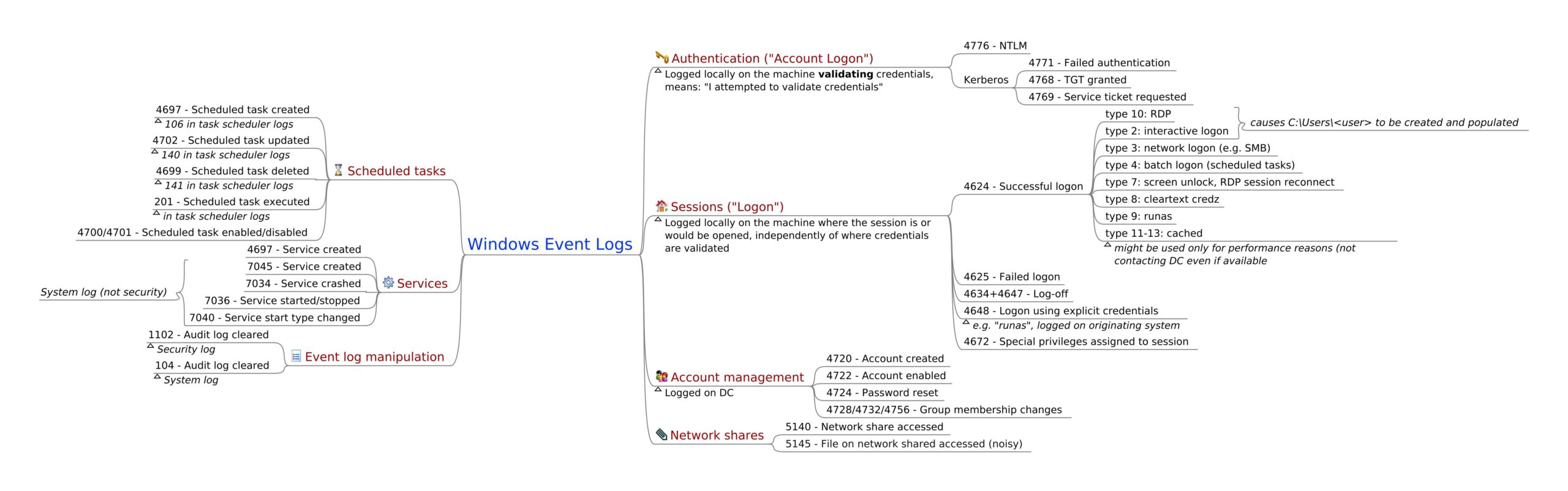
MENASEC - Applied Security Research: An overview of Windows EventID 4648 - Logon with explicit credentials
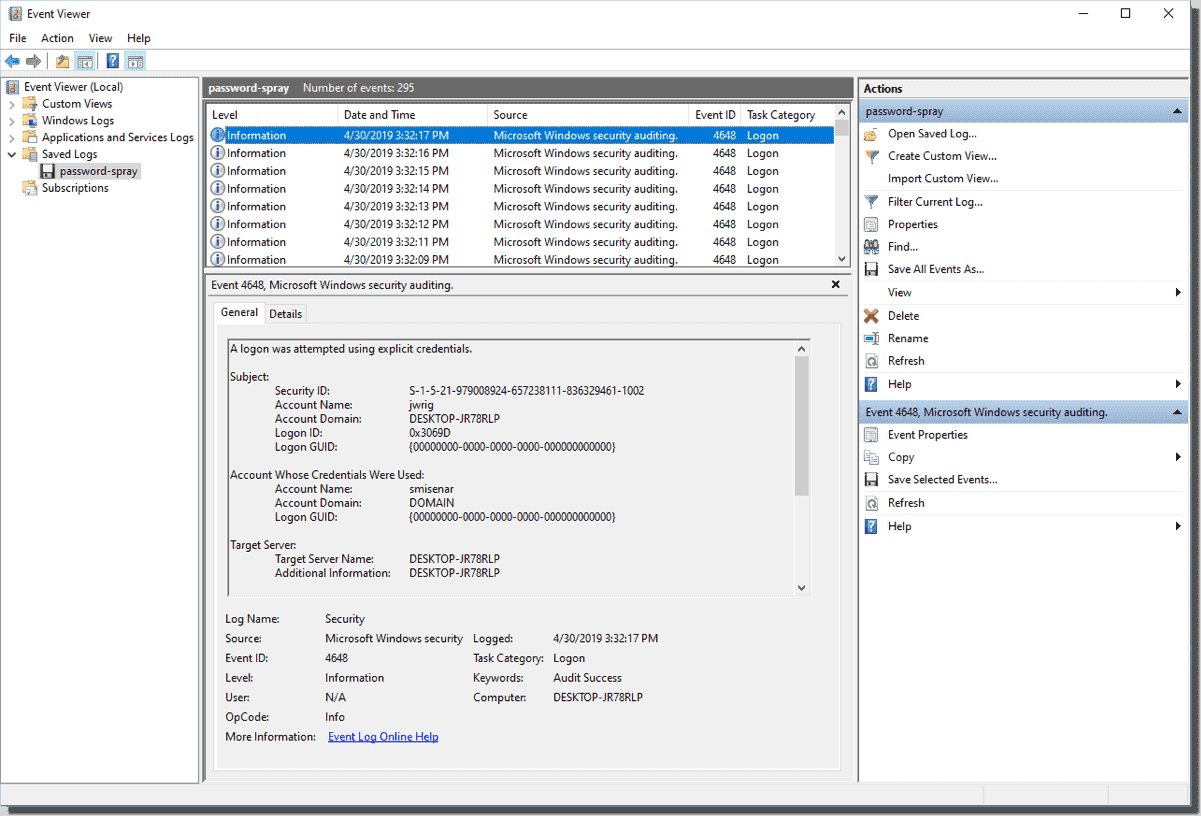
Using the Convert-EventLogRecord function alongside the Get-WinEvent PowerShell cmdlet to search Windows event logs – 4sysops

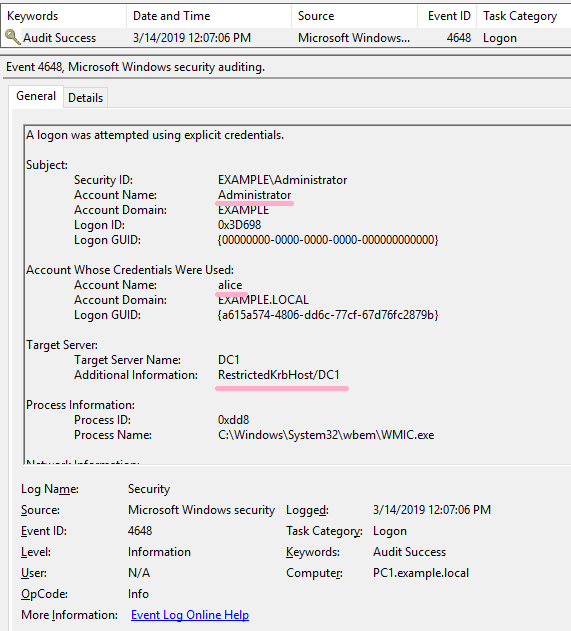
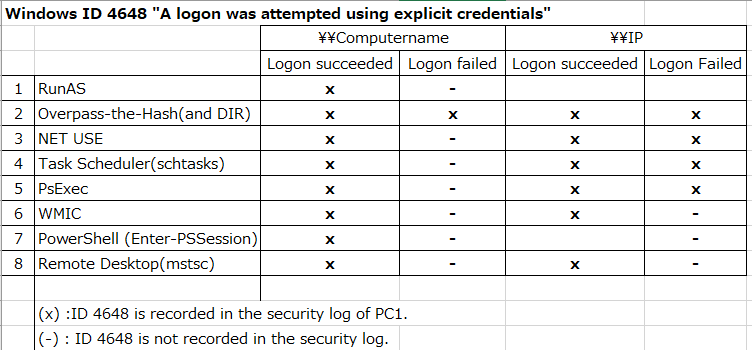
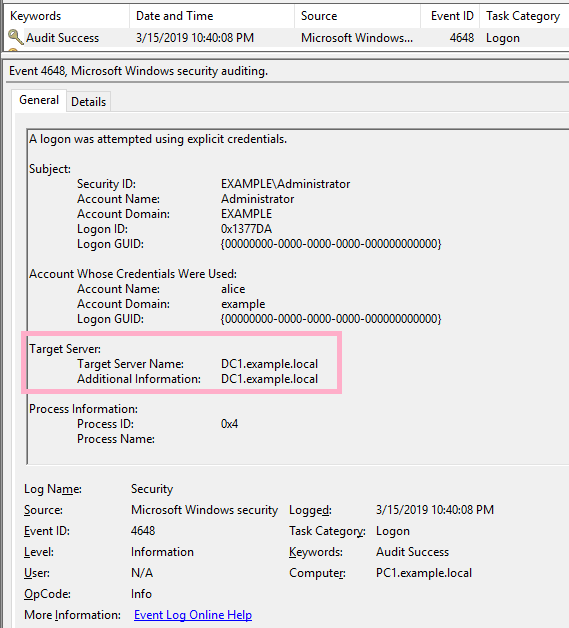



![4648: A Logon was Attempted Using Explicit Credentials [Fix] 4648: A Logon was Attempted Using Explicit Credentials [Fix]](https://cdn.windowsreport.com/wp-content/uploads/2022/12/Untitled-design-22-1200x1200.png)